Data privacy, data protection, and data security are not synonymous. They are complementary and all aspects should be embraced by organizations to guard their personal and sensitive data
For most organizations, data is the one of the most important assets. Many operations revolve around the collection, use, and sharing of data and information. Organizations may adopt a variety of data management practices and processes to organize and define data, but they may not apply appropriate rigor for ensuring the privacy of that data – or may not understand the need for providing protection and security of the organization’s data. As regulations to support enhanced data privacy become more common, it is essential that all data management and insurance professionals understand and apply the concepts of data privacy, data protection, and data security.
Basic Definitions
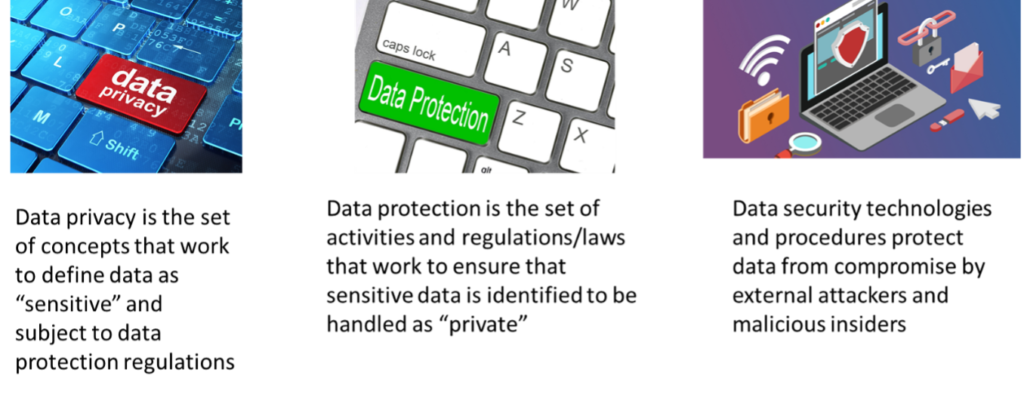
Data privacy is an area of data management that involves the proper handling of sensitive data to ensure confidentiality and accuracy. “Sensitive data” includes personal data and other confidential data, such as certain financial data and intellectual property data. The term “sensitive data” is often used in regulatory requirements to identify the data that should be subjected to data privacy approaches.
Data protection is the set of activities and regulations/laws that work to ensure that sensitive data is identified to be handled as “private”, available for use by authorized people and processes, and that the applied protection meets applicable regulations and laws.
Data security is the development of standards, safeguards and measures taken to prevent any third party from unauthorized access to data, or from any intentional or unintentional alteration, deletion, or disclosure of data. It focuses guarding data from malicious or accidental attacks and prevents the exploitation of data. Most data security protocols are technical, but some are human-based procedures.
Data privacy concepts, data protection activities, laws, and regulations, and data security technologies and procedures combine to allow organizations to operate with confidence that their critical, sensitive, and personal data will not be compromised.
Importance of Data Privacy
Data privacy is an essential part of ensuring two main business imperatives:
- Asset Management: Data is one of the most important assets for any organization, regardless of industry, size, etc. Companies find enormous value in collecting, sharing, and using data from a variety of sources for many reasons. It is crucial that businesses, especially insurers, strive for transparency in how they request consent to keep personal data, use business sensitive data (e.g., intellectual property, financial data, etc.), abide by their privacy policies, and manage the data that they’ve collected according to accepted processes. Clearly defined data privacy policies and consistently implemented data protection and data security processes and technologies are vital to building trust with management, employees, customers, and partners who expect their sensitive data to be safe and secure.
- Regulatory Compliance: Managing data to ensure regulatory compliance could be more important than meeting expectation of staff, customers, and business partners. Most organizations must meet legal responsibilities about how they collect, store, and process personal data. Non-compliance could lead to fines and a loss of operational respect. Consequences (e.g., lost revenue and lost trust and reputation) could have dramatic negative results.
Steps to Effective Data Privacy, Data Protection, and Data Security
Every organization will approach developing and sustaining an effective approach to safeguarding sensitive and critical data differently, but all should follow these foundational steps:
- Create a set of policies focused on achieving and maintaining data privacy. Include the types of data to be evaluated for privacy needs, and identify the major points to be included in the policies, then create and implement a data classification scheme that defines public data, personally identifiable data (PII), confidential business data, etc. Follow all applicable regulations and laws when developing the data privacy policies and data classification levels.
- Appoint a data privacy officer or data protection officer in addition to the technical data security team. Align the data privacy and data protection activities with the data governance and other data management programs.
- Create and implement a communications plan and a socialization plan for instilling the data privacy policies and their concepts into the organization
- Inventory the organization’s data based on the data privacy policy and the appropriate laws and regulations, and classify the data according to the data classification scheme
- Identify the processes for data protection for each data classification stage above “public”. Different levels may require different forms of data protection processes.
- Identify the data security packages/applications and procedures to fulfill the identified data protection processes – and implement them. Ensure that the technical data security team is aligned with the data privacy and data protection processes and policies.
- Create a plan for regular evaluation of data according to the data privacy policies, adapt the data protection processes based on changes to the data privacy policies, and revise the data security applications and procedures according to the changes in data protection processes. Maintain the alignment with data governance and related data management initiatives.
Conclusion
The goal of effective data privacy is achievable if organizations focus on the three parts: data privacy policies and responsibilities, data protection processes, and data security applications and technical implementation.







